11th Annual MSP 501 Identifies World’s Most Forward-Thinking MSPs & Leading Trends in Managed Services June 7th, 2018: CTG Tech ranks among the world’s 501 most strategic and innovative managed service providers (MSP...
CTG Tech has partnered with ACA Optimist Club in efforts to maximize donations and contributions for Hurricane Harvey victims and refugees. With your help, we will be able to provide necessary supplies that are a dire n...
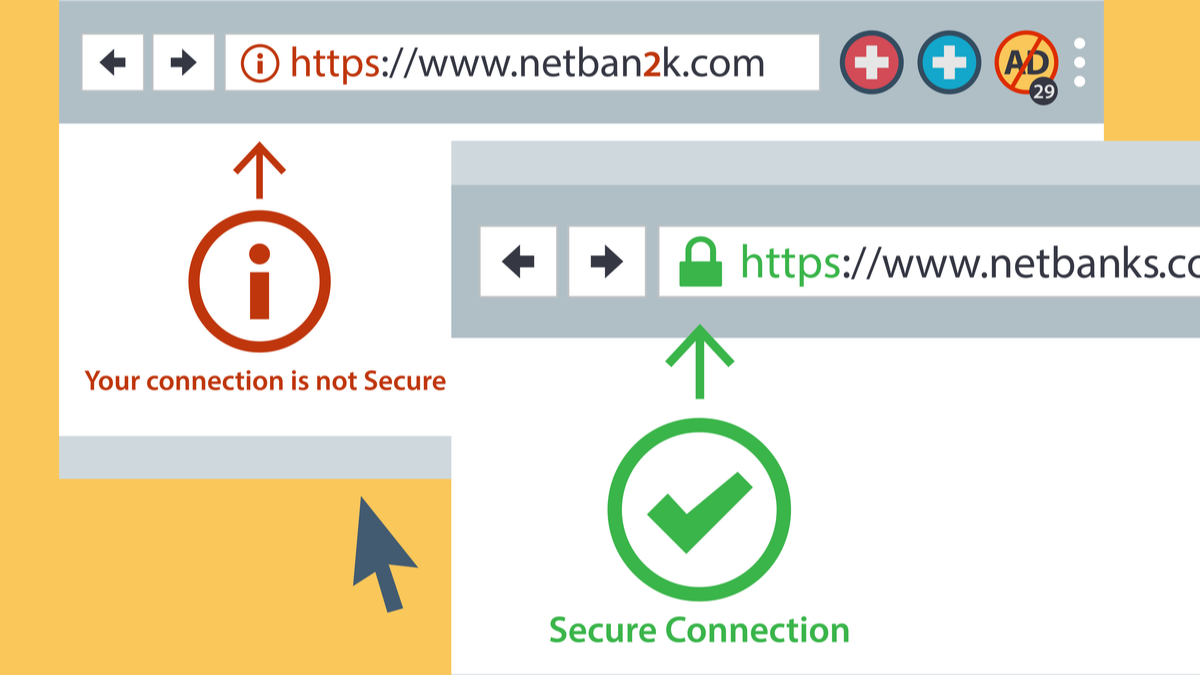
Protect Yourself From Fraudulent, Fake, and Scam Websites Managed cyber security services is becoming a trend as Fraudulent, fake, and/or scam websites are all over the internet, and cyber-criminals are great at being co...
Snapchat released an update and with it unveiled a new feature called “Snap Map.” This new feature allows users to see their friends’ locations and view exciting things that may be happening all over th...
CTG Tech, LLC Ranked Among Top 501 Managed Service Providers by MSPmentor June 2017: CTG Tech ranks among the world’s most progressive 501 Managed Service Providers (MSPs), according to MSPmentor’s 10th-annual MSP...
The majority of Americans (77%) own a smartphone, and we use them for everything! Capturing pictures and videos, staying connected with friends and family, meeting new people, banking and shopping, organizing our schedul...
EOL (End of Life) Machines and their Risks Using machines that have exceeded their lifetime is risky for your business. There are a variety of problems EOL (End of Life) machines can cause, and in the end, the risk isn’t...
Two million Android users could be infected with malware from apps on the Google Play Store. Nearly 50 apps were infected, including Pokémon Go, LEGO City My City, and FIFA Mobile. The first infected apps are estimated t...
Hiring IT services in Fort Worth is a big decision, regardless of the type of business you run or your industry. However, many business owners don’t give this decision the attention and consideration it deserves. In fact...
Finally finding and signing the contract with what seems like a quality provider of IT services in Dallas is often exciting for a business owner. It means they can finally outsource all IT services and ensure all their e...