What is a data breach?
The power of the internet is unmatched when it comes to exploration and innovation, but that power has also created an almost unstoppable force: hackers. These malicious ne’er-do-wells will stop at nothing to steal your personal information for their own gains. It doesn’t matter if you use one email account or 100: if these cybercriminals get their hands on your credentials, you will be in danger.
A data breach occurs when personal information such as passwords, banking information, and more is exposed. Data breaches can be intentional or accidental, but both are dangerous. Cybercriminals often work together to obtain personal information through social engineering, ransomware, malware, etc.
What happens to my passwords after a data breach?
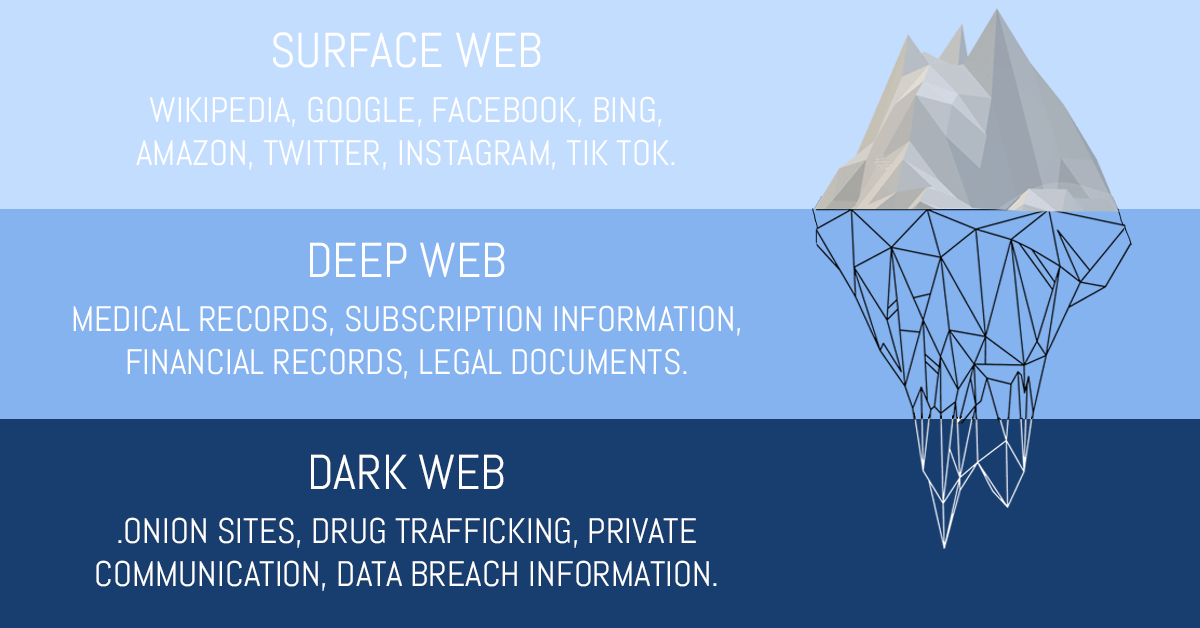
Your information has been involved in a data breach, now what? Your sensitive information will usually end up in a few places:
The Dark Web
The dark web is different than the World Wide Web we access everyday. We are used to using browsers such as mobile browsers on our phones, Google Chrome, or Internet Explorer. The dark web can only be accessed by a specific browser, known as Tor. Instead of .com, .gov, or .org like we are used to seeing, sites on the dark web use .onion.
There is no search engines (Google, BING) on the dark web either, so sites can only be accessed directly. Because the dark web was created for anonymity and privacy by the United States Navy in 2002, the websites on the dark web change often, and it’s the perfect place for criminals.
Hacker Forums
When large scale data breaches occur, such as the 2016 Yahoo data breach in which 500 million users were impacted, all the stolen information is compiled together and shared between criminals on a forum.
These files, containing passwords and other sensitive information are posted for sale, or sometimes even for free, for criminals to use to gain access to your accounts. If the password and username combination they have doesn’t work for one account they’ll try another. Then they’ll start at the beginning and try different variations of your password until they get in.
Future Data Breaches
Since we’re human and most of the time prefer ease over security, criminals know we are likely to have used the same credentials for multiple accounts, which is why it’s likely for you to be involved in more breaches after the first attack.
Think of it like the card game “Go Fish.” Each player (cybercriminal) has a stack of cards and all the players are trying to gather all the cards they need to make their set. Let’s say Player #1 has the key to decode the passwords, Player #2 has a list of passwords from one data breach, Player #3 has a list of passwords from another data breach, and Player #4 has usernames and other personal identity information (PII).
With the data combined, can cause a business to lose all its data and their customer’s data. The consequences of the data loss can hurt revenue, customer loyalty, and possibly have legal ramifications.

Biden’s Executive Order on May 12, 2021
President Biden has signed an executive order to help prevent data breaches by requiring federal organizations and IT Service Providers to share event logs and information on breaches that may impact or hinder the US Government. Information on known or discovered vulnerabilities is required to be shared as well.
“The Executive Order helps move the Federal government to secure cloud services and a zero-trust architecture, and mandates deployment of multifactor authentication and encryption with a specific time period. Outdated security models and unencrypted data have led to compromises of systems in the public and private sectors. The Federal government must lead the way and increase its adoption of security best practices…The Executive Order creates cybersecurity event log requirements for federal departments and agencies. Poor logging hampers an organization’s ability to detect intrusions, mitigate those in progress, and determine the extent of an incident after the fact. Robust and consistent logging practices will solve much of this problem.”
Once cyber criminals get the first door opened, they’ll start looking for the next key.
Tools such as haveibeenpwned.com and password managers can help you stay up to date on the security or risks of your passwords and accounts.
CTG Tech can help secure your business by implementing the best security practices, including integrating MFA to your business accounts, not re-using passwords, and taking advantage of password managers.