Social engineering is the use of deception and manipulation to convince us to hand over personal information that can be used for fraudulent purposes.
Who is behind this manipulation? For one thing, it’s not the guy in the hood hunched over a computer in a dark room. Cyber criminals rarely need to be a technical master-mind to have a pay day. Instead, they bank on the fact that we’re human, and therefore we’re vulnerable and make mistakes.
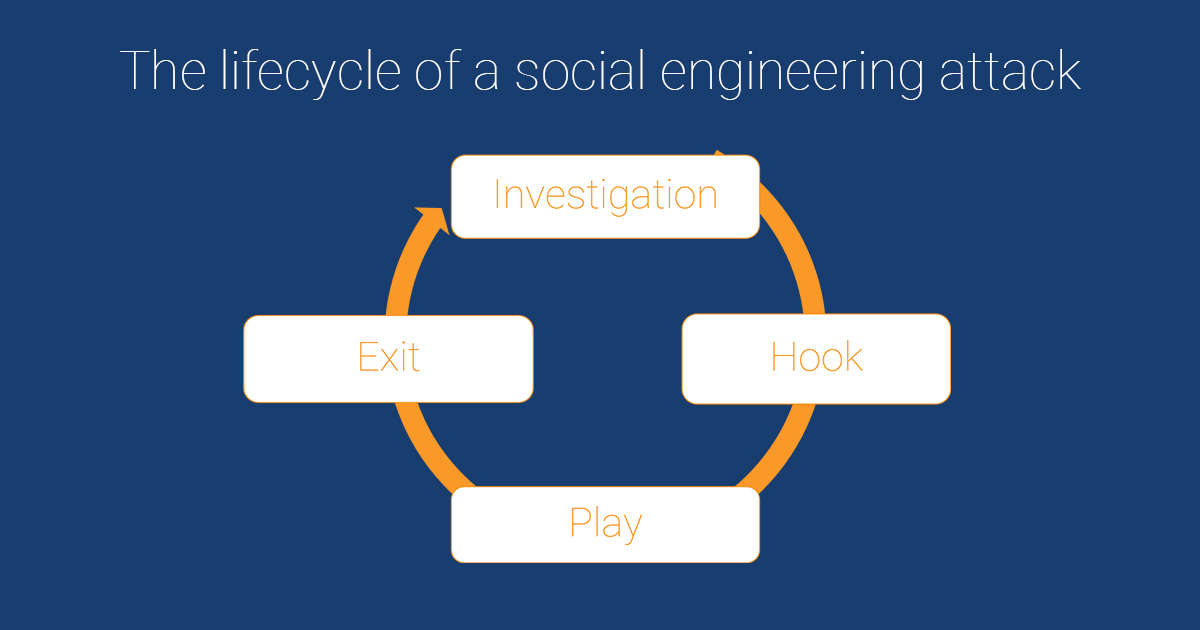
Cybercriminals begin their attacks with research, then they engage with us. The attack starts by spinning a false story in person, via email, call, or text. If their attack is not stopped here, they’re likely to succeed.
Once they have you hooked, they execute the attack. It could be that they got away with your log in credentials, other personal information like banking accounts, or even infecting your business with malware.
Con Artists use similar tactics as social engineers to prey on our vulnerabilities. Here are the top three vulnerabilities they target:
1- Respect for Authority
Social engineers exploit our nature of respecting authority and our fear of getting in trouble.
2- Desire to be Please
Social engineers rely on our instinct to be helpful.
3- Guilt / Sympathy
They create situations designed to attract our sympathetic feelings in order to play into their trick.
“Hacker’s don’t hack computers anymore, they hack humans.”
The right story, voice, or body language can give them the advantage of exploiting our biggest weaknesses.
Example #1 – 70% of phishing attacks begin with social engineering
Friday afternoon, your office assistant receives an email that appears to be from you or another supervisor at your company…
I need you to take care of this immediately, and before 5 o’clock; I have a meeting so I can’t.
We have an overdue balance of $50,000 on one of our critical accounts that needs to be paid.
Please go to this link and enter our account information and send the payment. James feels a sense of urgency from the email, but also because it’s Friday, and the work week is almost over. This leads him to dismiss that sender’s email address is not from the company domain and his respect for authority causes him to react quickly to the request and take care of it.
As soon as he’s submitted the information, and sent over the payment, he logs off and heads home for the weekend.
No one realizes until next Monday that the company has suffered detrimental loss; not only financially, but ransomware has encrypted your company’s files, and the criminals are demanding more on top of the $50,000 they have already stolen.
You had to fire James to eliminate the chance of this ever happening again; that is, if your company survives this attack, and you know statistically, there’s a 60% chance after a breach your business won’t make it longer than six months.
Example #2- The average cost of data breach in the US is $8.64M
“Drake” walks into your office and greets your receptionist, Melanie, warmly and engages in pleasant conversation with her…
Drake: “Good morning ma’am, how are you doing today? That blouse really brings out the color of your eyes.”
Melanie: (blushes) “Oh, thank you!”
Drake: “Of course!”
Melanie: “What can I help you with today”
Drake: “Well ma’am, I’m Drake from your tech support company, and I’m pretty sure we’ve spoken on the phone before. I’ve been assigned to troubleshoot some of the printer issues. I’ve been told it’s a pretty vital issue that needs to be fixed immediately. It won’t take me long, but I will need you to show me to the server room and point me in the direction of your printers, if you don’t mind.”
Melanie: “Sure, I’d love to help, just follow me.” Melanie’s desire to be helpful, and continue speaking to such a pleasant fellow, distracts her from any skepticism she may have felt before. She dismisses any other alarm bells in her head, especially since he’s already proved he can be trusted, and she believed they have even spoken before.
She leads him to the server room, while he keeps the conversation flowing. Once he’s in the server room, she walks back to the front desk and he proceeds to plug a USB into your server and upload a virus to your company’s network and escapes out the back door undetected.
Melanie never mentions anything of it, and figures he left after finishing the upgrades.
Little does she know that “Drake” uploaded spyware into their servers. Statistically, companies aren’t aware of breaches until 280 days after the attack. In the meantime, “Drake” is collecting credentials of every employee, bank accounts, customer information, and other confidential information. This information he could hold ransom or sell on the dark web for the highest bidder.
The security of your company is only as strong as your employee’s awareness. Social Engineering attacks are more successful to companies who don’t invest in regular security trainings for their employees.
It’s easier to hack humans than it is to hack computers nowadays. If a cybercriminal can manipulate your employees to give them the information they need, the hardest part is already done. Your employee opened the door (email, text, etc.) to your business without asking any questions. There’s only so much that technology can protect us from, the rest is up to you and your employees.

