Protect Yourself From Fraudulent, Fake, and Scam Websites
Managed cyber security services is becoming a trend as Fraudulent, fake, and/or scam websites are all over the internet, and cyber-criminals are great at being con-men. They are so good at being fake that people fall for them all the time. It’s important to arm yourself with the knowledge to know how to check if a website is fake, fraudulent, or trying to scam you. Also, you may have ended up on the site from a phishing attack email scam that looks and appears like any other normal email. Everyone should teach themselves on how to recognize a phishing attack.
1. Use your common sense!
When you arrive to a website in question, think about how you got there. Was it from a link you clicked in an email, or an advertisement from Facebook? Think before you click.
Red Flag #1 Spelling mistakes – they take away from the credibility of the website and the information on it, and in most cases are a sure sign that something is a scam.
Red Flag #2 Advertisements – An over-abundance of ads, ads that require you to enter personal information, complete a survey, or ads that redirect you to another page. Cybercriminals sometimes use ads to make money because every time someone clicks on them, it’s money in their pocket. They will place ads on websites that make it easy to accidently click on them. Be careful.
2. Trust Seals and Contact Information
Contact information is usually a good indicator of someone you can trust. It won’t hurt to try provided numbers or emails if you question their legitimacy. If you find yourself engaging with website that doesn’t provide contact information, or the contact information doesn’t seem right, then back out.
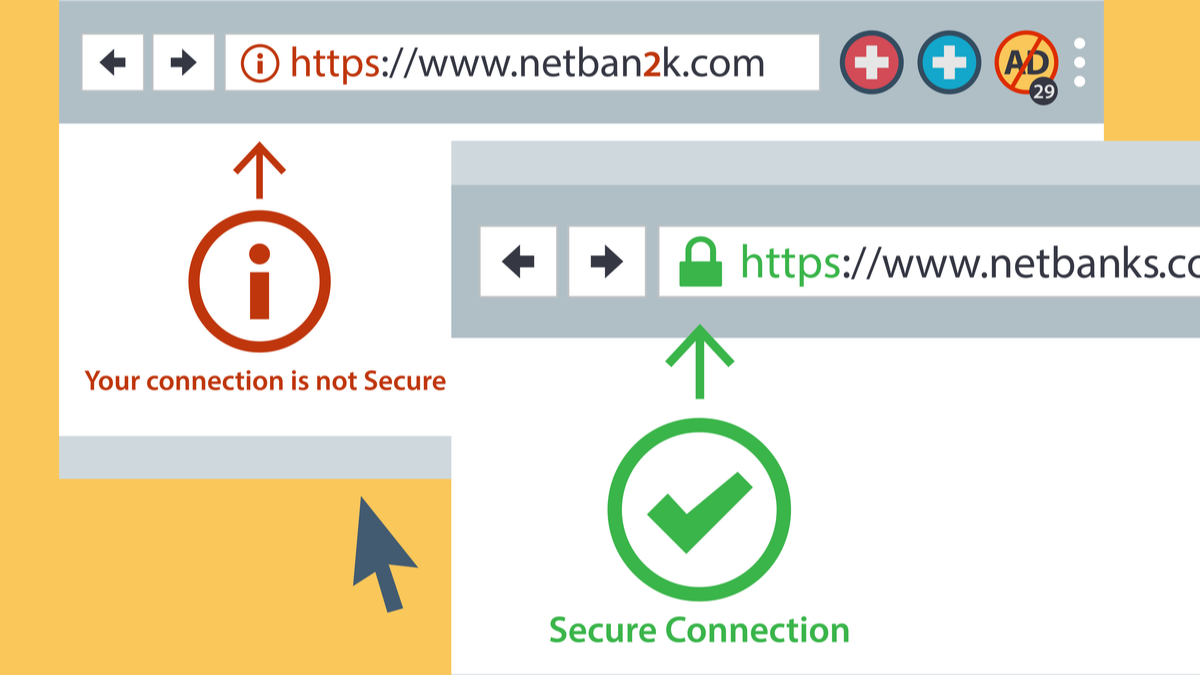
3. Pay attention to the address bar; you can learn a LOT from it
Most browsers will let you know if the connection is secure or not, before the page even loads all the way. If it’s not, it will warn you with a message saying “your connection may not be secure, click here to go back to safety.”
If it’s secure you’ll notice a few different things in the address bar. You may notice a padlock; the address bar may be green, and “https” as a part of the URL.
If there is a padlock next to the URL, then the connection between you and that website is secure. You can view the website’s security details by clicking on the padlock in some browsers.
It’s even better when you see the padlock and a green address bar. Those two things combined mean any information between you and the website is protected using something called a certificate. When a website uses a certificate, the URL will contain HTTPS. Your connection is secure, information you enter is encrypted, and it cannot be intercepted.
But don’t stop there! Always keep an eye out for domains that look like they belong to a trusted site, but have extra characters, spelling errors, or domain extensions that lack credibility like “.biz” or “.info.”
4. Last, but not least, check the website’s reputation
Google reviews for the website. It’s a lot easier to learn from the mistakes of others than having to learn the hard way.
There are websites that will do the investigating for you, all you have to do is type in the site’s URL.
- www.scamadvisor.com
- Google’s Safe Browsing Transparency Report
- Check with the Better Business Bureau
If you do come across a website that you believe is fraudulent, fake or a scam you can report them to Google’s “Safe Browsing” or Mozilla’s “Protect the Fox.” The internet is full of endless opportunities and can be a great tool for whatever you do, but your safety needs to always remain your first concern while browsing it.
In Conclusion:
If you are still unsure whether a website maybe a scam or not contact your IT Services provider in Dallas and have them check it out for you. Every business should have network security to ensure your computers are protected and safe to browse. If you look at our cyber security packages you can get an idea on why we were ranked the managed service providers.
Contact us today or fill out the form for a free consultation and network security audit. And regardless you should always have a backup and a business continuity plan in place so that if your data was ever compromised, you can always restore your data and continue working.